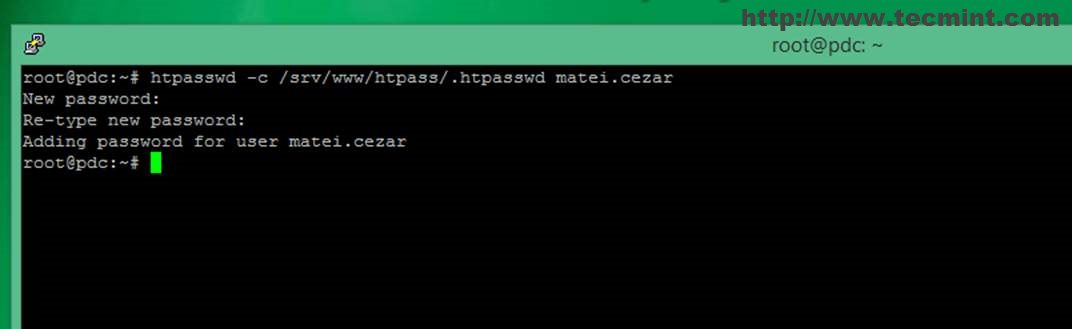
$ htpasswd -b htpasswd password Creating an HTPasswd file using Windows To use the HTPasswd identity provider, you must generate a flat file that contains the user names and passwords for your cluster by using htpasswd. Is there any tool that given the crypted password I can try to brute force (or use a dictionary attack) and get the original password? There are a lot of MD5 password crackers but they don't state if they work for htpasswd generated passwords.
- Short answer: no. Try cheating: at the same time you write the login and encrypted password to your htpassword file, write the login and unencrypted password to a hidden file accesable only to you for future reference.
- The Apache HTTP Server can use a.htpasswd file referenced from a.htaccess file to create restricted protected areas. The.htpasswd file contains rows corresponding to a pair of username and password separated with a colon character. The password is encrypted using the UNIX system's crypt method and may use MD5 or SHA1. This.htpasswd generator creates passwords that are hashed.

Released:
Library to work with htpasswd user (basic authorization) and group files.
Project description
# htpasswd [](http://travis-ci.org/thesharp/htpasswd)
## Descriptionhtpasswd is a library for working with htpasswd user (only basic authorization) and group files. It supports CRYPT and MD5 encryption methods. To actually use MD5 encryption method you MUST have an openssl binary installed into system $PATH.
## Dependencies- Python 2.7 or 3.3 or 3.4- [orderedmultidict](http://pypi.python.org/pypi/orderedmultidict/0.7) >= 0.7- [future](https://pypi.python.org/pypi/future)- [nose](http://pypi.python.org/pypi/nose/) >= 1.1.2 (for tests)
Sql Server Decrypt Password
import htpasswd
- with htpasswd.Basic(“/path/to/user.db”) as userdb:
- try:
- userdb.add(“bob”, “password”)
- except htpasswd.basic.UserExists, e:
- print e
- try:
- userdb.change_password(“alice”, “newpassword”)
- except htpasswd.basic.UserNotExists, e:
- print e
- with htpasswd.Group(“/path/to/group.db”) as groupdb:
- try:
- groupdb.add_user(“bob”, “admins”)
- except htpasswd.group.UserAlreadyInAGroup, e:
- print e
- try:
- groupdb.delete_user(“alice”, “managers”)
- except htpasswd.group.UserNotInAGroup, e:
- print e
To use MD5 encryotion, add mode='md5' to the constructor:
with htpasswd.Basic(“/path/to/user.db”, mode=”md5”) as userdb
## Provided methods
### Basic- __contains__(user)- users- add(user, password)- pop(user)- change_password(user, password)- _encrypt_password(password)
### Group- __contains__(group)- groups- is_user_in(user, group)- add_user(user, group)- delete_user(user, group)
## Exceptions
### UserExistsRaised by Basic.add if user already exists.
### UserNotExistsRaised by Basic.delete and Basic.change_password if there is no such user.
### GroupNotExistsRaised by Group.delete_user if there is no such group.
### UserAlreadyInAGroupRaised by Group.add_user if user is already in a group.

### UserNotInAGroupRaised by Group.delete_user if user isn’t in a group.
### UnknownEncryptionModeRaised by _encrypt_password if mode is not ‘crypt’ or ‘md5’.
Release historyRelease notifications | RSS feed
2.3
2.1
2.0
1.0
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
| Filename, size | File type | Python version | Upload date | Hashes |
|---|---|---|---|---|
| Filename, size htpasswd-2.3.tar.gz (3.8 kB) | File type Source | Python version None | Upload date | Hashes |
Hashes for htpasswd-2.3.tar.gz
How To View Encrypted Password
| Algorithm | Hash digest |
|---|---|
| SHA256 | 565f0b647a32549c663ccfddd1f501891daaf29242bbc6174bdd448120383e3d |
| MD5 | 73607c4b3443786dbc591616578c63ea |
| BLAKE2-256 | b92f8b76f8b77125b75c3532966f3291f9e8787268be65fc4c9694887cba9375 |